Digitally sign escrow material
Add proof of origin and authenticity to the information deposited with Escrow4all.
Signing and signature verification requires a keypair: a private key and a complementary public key. The sender uses the private key to sign the document. The recipient uses the public key to verify the document signature.
GnuPG
Most Linux distributions already have GnuPG installed. If not, open the Terminal app to install GnuPG.
On Red Hat Linux execute the following command:
#!/bin/bash
sudo yum install gnupg
On Debian Linux execute the following command:
#!/bin/bash
sudo apt update
sudo apt install gnupg
Keypair
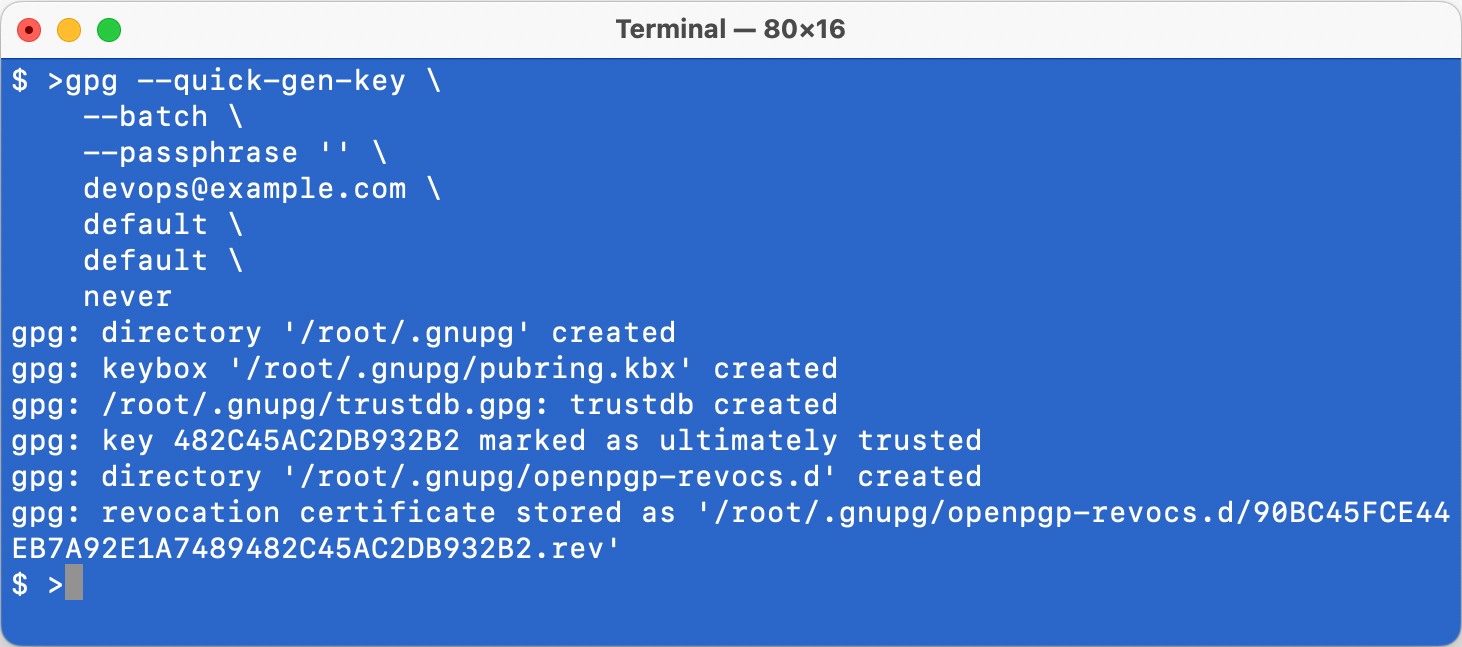
To generate a new keypair, execute the following command in the Terminal app:
#!/bin/bash
gpg --quick-generate-key \
--batch \
--passphrase '' \
devops@example.com \
default \
default \
never
Always store a backup of the keypair in a safe location. Execute the following command to export the keypair:
#!/bin/bash
gpg --export-secret-key --armor devops@example.com > ~/safe/location/keypair.asc
The public key should be made available to Escrow4all. Execute the following command to export the public key.
#!/bin/bash
gpg --export --armor devops@example.com > ~/public/location/public-key.asc
Note
Generating a keypair is a one-time job and should not be scripted.
Use the same keypair for subsequent submissions!
Warning
This example generates a passwordless private key. This method should be used only for unattended/automated processes.
For any other use case we do not recommend this!
Sign
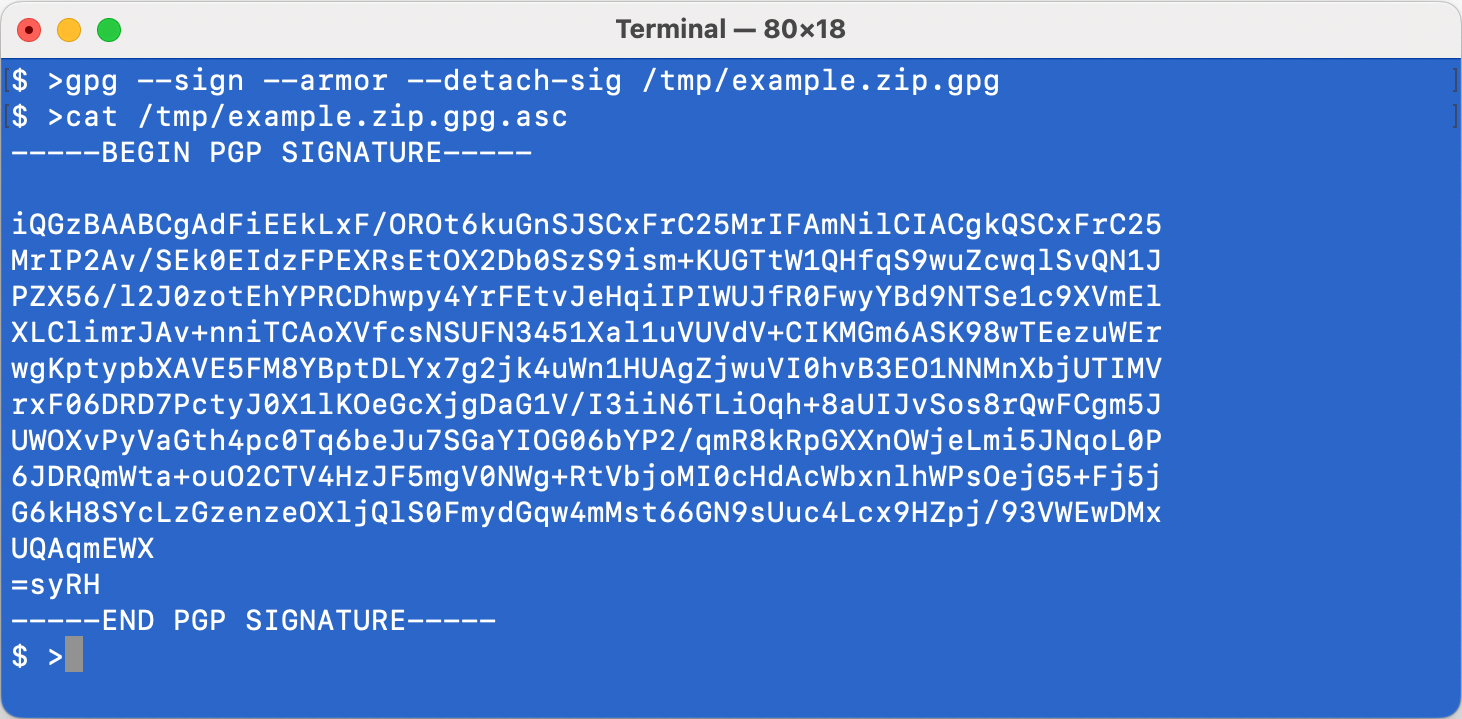
Execute the following command to digitally sign a file/document:
#!/bin/bash
gpg --sign --detach-sig --armor /tmp/example.zip.gpg
The armor option tells GnuPG to store the signature as a plain-text file. When armor is omitted the digital signature is a binary file.
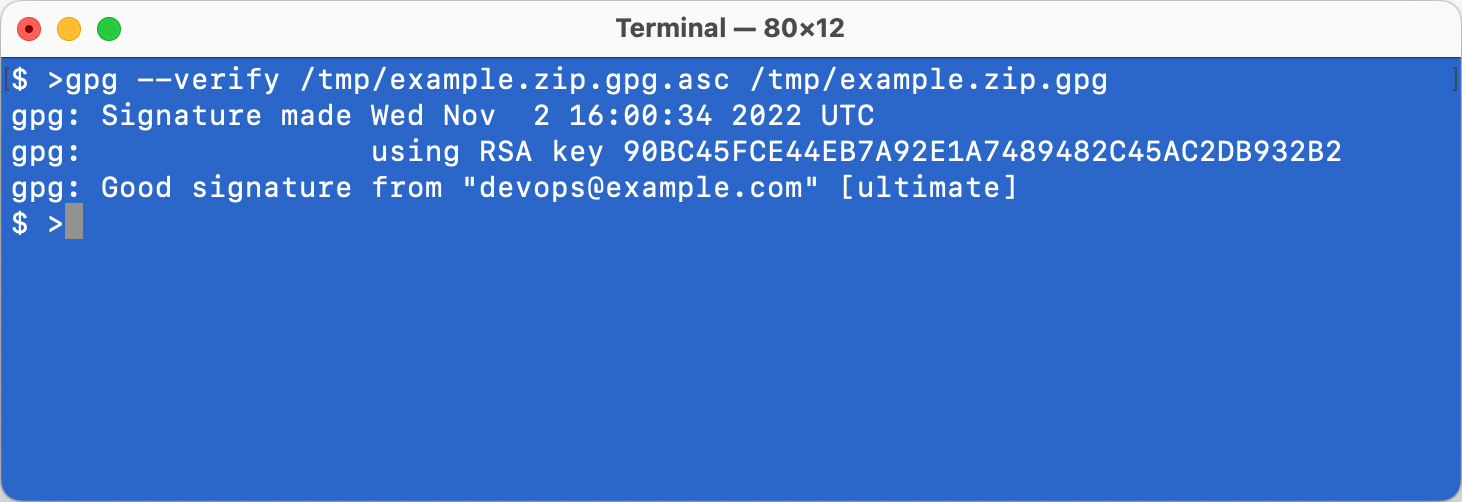
Verify signature
Execute the following command to verify the digital signature:
#!/bin/bash
gpg --verify /tmp/example.zip.gpg.asc /tmp/example.zip.gpg